Yirla Audit and Logging architecture
Architecture Component Breakdown
• User Action Ingestion: The process begins when users perform actions such as logging in, making API calls, or changing configurations.
• Application Processing: The Yirla Application Layer (powered by FastAPI) enforces Role-Based Access Control (RBAC) and injects tenant context before generating audit events related to authentication and authorization checks. This also includes tracking data access (read/export) and administrative or support actions.
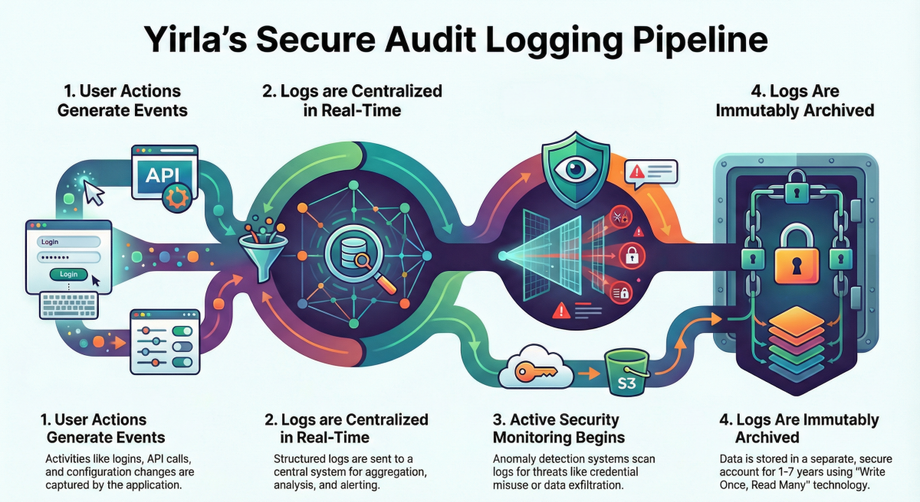
• Centralized Aggregation: Logs are funneled into Datadog for real-time ingestion. These logs are structured in JSON format and protected by MFA and RBAC, with active alerting for anomalous patterns.
• Security Monitoring: AWS GuardDuty consumes these logs to perform anomaly detection, monitoring for credential misuse and data exfiltration.
• Immutable Archiving: Logs are stored in a Long-Term Audit Archive using Amazon S3 with Object Lock. This storage is highly secure:
◦ It uses a Write Once, Read Many (WORM) model.
◦ Data is encrypted with AES-256 and kept in a separate AWS account.
◦ Retention is set for 1–7 years, and even administrators cannot delete or modify the records.
• AWS Control Plane Integration: AWS CloudTrail monitors the underlying infrastructure—including IAM changes and access to RDS, KMS, or Secrets Manager—and streams these logs directly to the immutable S3 storage.